Redundancy isn’t the same as reliability. The gap is your front door for data. Read on for a comparison of single-cloud, multi-cloud, and decentralized cloud environments – with Pocket Network’s Decentralized Access Layer as a reference. Prologue: The day redundancy didn’t save the launch The launch window was tight. A new pricing page, a refreshed…
Category Archives: News
Pocket Network’s Decentralized Data Stack: Service, Source & Supplier
In this piece, we present a map and vocabulary to navigate the decentralized infrastructure of Pocket Network. After skimming, you’ll have a clear picture of the puzzle pieces that fit together to make Pocket Network efficient, resilient, and fruitful for its participants. You’ll learn about each role, see how it may apply to you or…
Blockchain Governance Models Explained
Most people don’t buy a token because of governance. They buy the story, the product, and the community. That’s fine. But once you’re holding the bag, the stuff that keeps value from dumping, maintains pricing, supply discipline, and reliable access comes from how a network is governed. In other words, you don’t need governance to…
Welcome, Shannon: The new era of permissionless access is here
June 3rd marked a historic milestone for Pocket Network: the successful launch of Shannon, the protocol’s most ambitious and comprehensive upgrade to date. This release has officially positioned Pocket as the world’s first permissionless API network, unlocking a decentralized future for data access across blockchains and APIs. Shannon Unleashed The June activation of Shannon completed…
Centralized vs. Decentralized Data Ingestion for AI
Why Data Ingestion Matters in AI AI agents in crypto live and die by the blockchain data they consume. Whether it’s a predictive trading bot reacting to mempool surges, an on-chain oracle feeding real-time price ticks to a DeFi protocol, or an AI service that generates dynamic NFT artwork from the latest block events, your…
From Billions to Trillions: The Future of Pocket Network
On June 3rd, 2025, Pocket Network performed a hard fork into the Shannon upgrade, the culmination of four years of learning and two years of active development work. The upgrade, which made Pocket a Cosmos native chain, unlocked three key areas of functionality: Prior to the upgrade, the Morse version of the network had served…
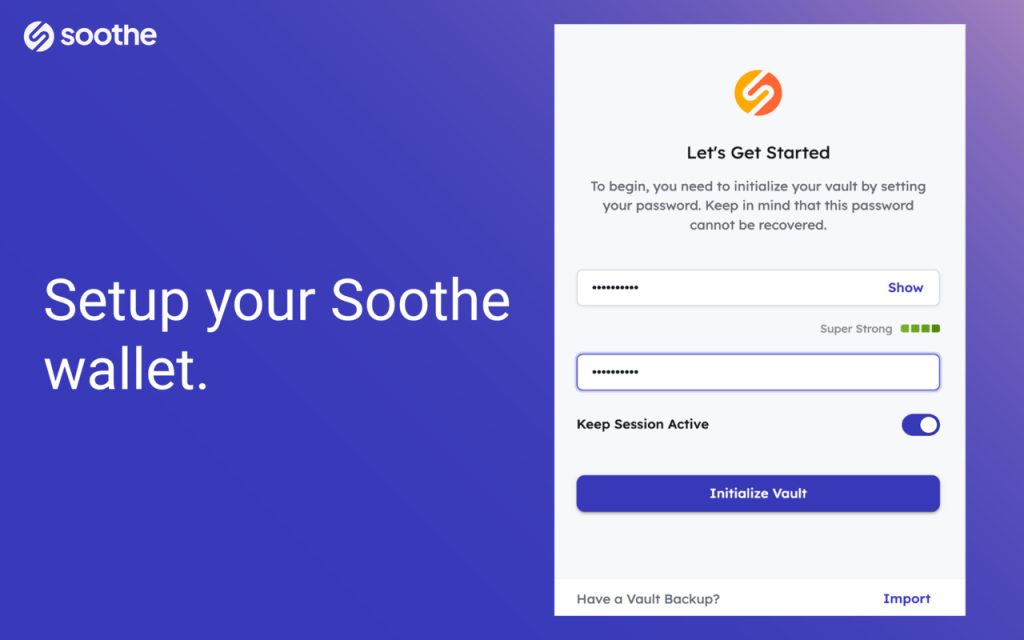
Using Soothe Vault To Prepare For The Shannon Upgrade
If you’re looking to manage your Morse mainnet account for the Pocket Network and prepare for migration, the Soothe Vault Chrome extension provides a streamlined way to import your wallet. This guide will walk you through each step of the process. Step 1: Visit the Soothe Website and Download the Extension First, open your Chrome…
Bonding Curves and Dynamic Pricing Explained
On May 16, 2024, the crypto meme world was jolted when a Solana-based meme coin platform, Pump.fun, was compromised by hackers who manipulated its bonding curve contracts. The exploit resulted in abrupt price swings and heavy losses—underscoring how powerful yet precarious these automated pricing mechanisms can be. Despite the exploit, bonding curves remain a foundational…
Common Web3 Gateway Issues and How to Solve Them
Web3 gateways serve as critical bridges between users and decentralized networks, but they often face performance, scalability, security, and data synchronization challenges. Below, we explore the key issues and actionable solutions to optimize these gateways for a seamless decentralized experience. Understanding these challenges and their solutions is vital for ensuring a seamless experience as users…
Security Risks in Cross-Chain Interoperability
In summary, Cross-chain interoperability allows different blockchain networks to communicate and transfer assets seamlessly. However, it also introduces security vulnerabilities where hackers can exploit flaws. Recent history has shown multiple attacks on bridge protocols, resulting in hundreds of millions of dollars stolen. These vulnerabilities stem from various sources, including contract vulnerabilities, validator takeovers, and fundamental…