Pocket Network, after the Shannon upgrade, has evolved past RPC endpoints; it is now the open, crypto-native access layer for verifiable data. You can run your own access layer (PATH Gateways), prove the quality of the data you return (QoS and relay proofs), align economics directly with usage—making Pocket a full, modular, and decentralized infrastructure layer for data.
This post gives you a simple, high-level map of building on Pocket in the Shannon era—how the access layer works, how supply plugs in, and where pricing and quality controls show up in real projects. By the end, you’ll understand the core model, the main ways teams turn it into products.
First, a quick mental model
Before we talk about what you can build, it helps to zoom out and look at the basic flow of a request through Pocket. A call comes in at the edge, gets routed across the network, verified for quality, and then settled on-chain. Along the way, different actors handle different pieces — one receives the request, another routes it, another serves the data, and the protocol itself records the outcome and aligns costs with rewards.
Think of it as a loop: request → route → verify → prove → settle → learn. That’s the cycle every relay follows, and it’s the foundation the rest of this guide builds on. In the next sections, we’ll dive into the roles inside that loop and show how developers can run, extend, or combine them into real projects.
Builder Tracks in Shannon (What You Can Run, Earn, and Use)
Below are the main ways developers plug into Pocket Network today. For each track, we outline what you operate, how value flows back to you, and the tooling that gets you shipping fast.
Operate a PATH Gateway (your own access layer)
Run the entry point that your apps call. PATH handles request intake, routing, and proof packaging off-chain, while your staked on-chain Gateway signs work. You can self-host to control latency, auth, and pricing, and qualify for protocol-level rebates as your daily volume rises (0% to 40% based on compute units per day).
Why it matters
Running a PATH Gateway means you’re not relying on someone else’s RPC; you own the entry point your apps depend on. For developers, that means predictable performance, the ability to tune auth and routing to your needs, and QoS checks baked in by default.
For the protocol, every relay is proven and settled on-chain, keeping usage and rewards transparent. And at scale, the rebate system makes high-volume gateways economically attractive, ensuring the network grows with real demand.
Incentives
Gateway operators earn indirectly by capturing app traffic and can qualify for volume rebates, in which 10–40% of spent compute units (CUs) can be rebated if daily relay volumes cross defined thresholds, funded from the DAO’s rebate budget. Rebates are distributed quarterly, pro rata among eligible gateways, aligning revenue with real usage growth.
Read more on our rebate formula under Shannon.
Tools and Guides
- Getting Started: PATH Quickstart (<10 min) — Run PATH in Docker, check /healthz, send your first relay.
- Configuration Deep Dive: PATH Configurations — Reference for .config.yaml gateway settings, auth config, Helm values.
- Production Deployment: PATH Helm Guide — Setup via Helm with WATCH observability, Grafana dashboards, and RBAC considerations.
- QoS & Testing: PATH QoS Overview — Built-in verification logic and supported services. PATH Testing Guide — E2E and load-test walkthroughs.
- Developer Guide & Releases
- PATH Developer Guide — Full walkthroughs (Getting Started, Pocket Network Guide, example relays).
- PATH Releases & Container Registry — Latest versions and container tags.
- PATH Container Registry — Base Docker image for PATH.
- App Integration SDK: PocketJS SDK — For connecting apps to your own Gateway.
- Walkthrough from Pocket: App & PATH Gateway Walkthrough (~1 hr) — Step-by-step binary guide from the Pocket docs stack.
- Guides & Blogs: How to Set Up Your PATH Gateway (step-by-step blog with pricing and rebate examples).
Run a RelayMiner
RelayMiners are off-chain actors that process traffic flowing from gateways to suppliers. Their job is to route requests to the best available supplier, collect the responses, and package them into relay proofs that can be submitted on-chain. This is the step that transforms network traffic into measurable work, with each proof tying usage directly to compute units for settlement.
Why it matters
Without RelayMiners, Pocket would just be raw RPC forwarding. By enforcing routing logic and generating proofs, RelayMiners make every relay auditable, accountable, and payable by design. This protects applications with verifiable data paths, ensures suppliers are rewarded only for valid work, and keeps the protocol’s usage-based economics honest.
Incentives
RelayMiners don’t earn directly but are essential to the reward cycle. By generating valid relay proofs, they unlock payments for Suppliers and keep app costs tied to verifiable usage. Missed or invalid proofs result in forfeited rewards, ensuring RelayMiner accuracy aligns with the protocol’s reliability.
Tools and Guides
- RelayMiner Config (docs) — Full configuration reference.
- RelayMiner Setup (blog) — Quick setup steps in Shannon node guide.
- Exploring PATH Capabilities (article) — Walkthrough with sample config and CLI usage.
Become a Supplier
Suppliers are the staked providers (minimum of 60,000 POKT) that actually serve data to the network participants, such as a full node, an indexer, or other services. They register these services, connect them to the protocol, and respond to requests routed by RelayMiners. Reliability, latency, and consistency directly affect how often a Supplier is selected and how much traffic they handle.
Why it matters
Suppliers are the backbone of Pocket’s promise: verifiable, censorship-resistant access to data. For applications, they guarantee that requests don’t hinge on a single centralized RPC provider, while for the protocol, they bring diversity and redundancy. For operators, performance translates directly into opportunity, where more consistent uptime and lower latency mean more relays served and more rewards earned.
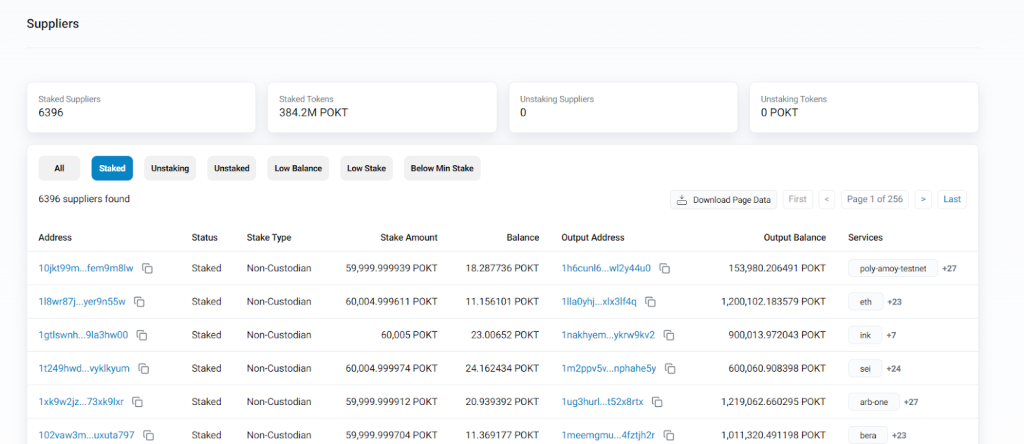
Top Suppliers on PockeNetwork. Source: Poktscan
Incentives
Suppliers earn POKT through usage-linked rewards: each valid relay is measured in compute units and settled on-chain via the claim—proof lifecycle. Earnings scale with traffic and quality. Relays that fail QoS checks (like archival validation) are excluded, so only valid work is rewarded.
For more information on the new incentive model under Shannon, please refer to our Tokenomics article.
Tools and Guides
- Supplier & RelayMiner Cheat Sheet — Stake, configure, and test a Supplier.
- RelayMiner & Supplier Config (docs) — How to connect a Supplier through a RelayMiner.
- Supplier Stake Config — configuration on how Suppliers submit a stake transaction (a prerequisite).
- Exploring PATH Capabilities (article) — Example of running a Supplier alongside a RelayMiner.
- Supplier FAQ — Common commands and patterns.
Publish a New Service
Services are the endpoints Pocket exposes through PATH; they can be anything from a chain RPC to a custom REST/GraphQL feed or an OpenAI-compatible LLM. By registering a service, staking as a Supplier, and routing through a RelayMiner, you can make your data source discoverable and consumable to any application connected to the network.
Why it matters
Services expand Pocket beyond blockchain RPC into a modular data marketplace. For developers, it means you can plug in new APIs and immediately serve them through permissionless gateways.
For applications, it creates more choice, from full-node RPC to specialized data feeds or AI inference. For the protocol, it broadens demand and ensures Pocket can support any open service with the same verifiable workflow of request → route → proof → settlement.
Incentives
Service operators earn through the Supplier track: each verified request routed to a service is converted into compute units and rewarded on-chain. Reliable, high-quality services capture more traffic; invalid or inconsistent responses are excluded by PATH’s QoS system, so incentives favor accuracy and uptime.
For more information on the new incentive model under Shannon, please refer to our Tokenomics article
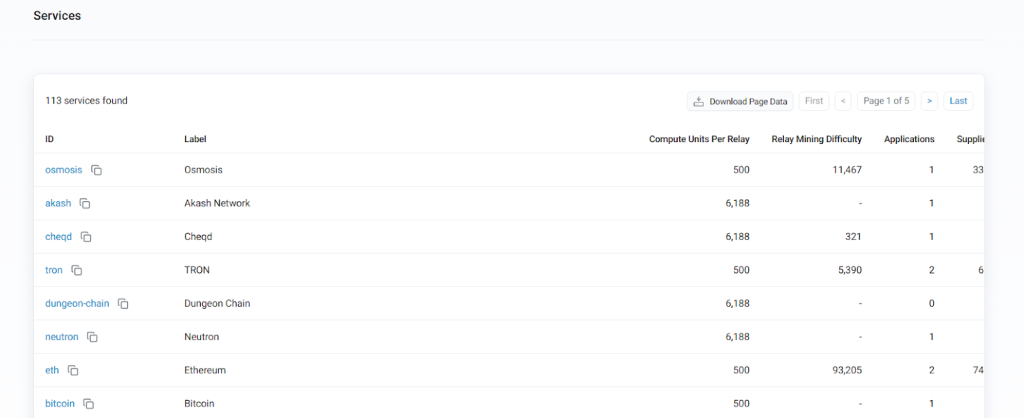
Services on Pocket Network. Source: Poktscan
Tools and Guides
- Create a Service (cheat sheet) — Add/query a service; set compute_units_per_relay
- Service FAQ (CLI queries & txs) — Common commands and patterns
- RelayMiner config (wire it up) — Point your RelayMiner at the backend you’re exposing
- Consume via Gateway (for testing) — Stake an App & Gateway, then send test relays.
Build with Applications
Applications are the on-chain accounts that pay for access to data through Pocket. To use the network, you stake your app and delegate it to a Gateway that routes and signs your traffic. The current minimum stake for Applications is 100 POKT, while Gateways require 1 POKT.
Why it matters
Staking an Application gives you predictable, usage-priced access (1 CU = 1 nano-USD), with every request metered, proven, and settled on-chain. You control where traffic goes (your own Gateway if you run one), you inherit QoS checks at the edge, and you can reason about cost because burn-to-pay ties spend directly to usage.
Incentives
Applications don’t earn; they consume. Your incentive is transparent, auditable cost, and the option to route through a self-hosted Gateway that can qualify for protocol rebates at scale (rebates kick in for high daily CU volume and are budgeted DAO-wide).
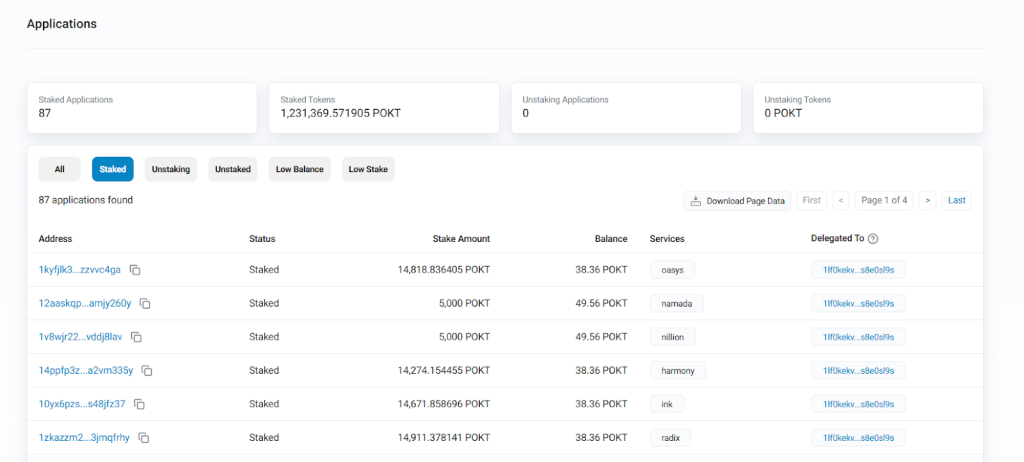
Staked Applications on PocketNetwork. Source: Poktscan
Tools and Guides
- Cheat sheet/quickstart: Stake app + gateway and send a test relay in 30 minutes.
- Application staking config: Application staking config reference (fields incl. stake_amount, service_ids).
- Application & Gateway FAQ: App & Gateway FAQs (staking/upsizing examples). dev.poktroll.com
- Application & PATH walkthrough: Configure PATH for Shannon + QoS matrix. dev.poktroll.com
- Application Stake Transfer — Instructions on how to transfer an application stake.
Run a Validator
Validators (full node runners) secure Pocket’s chain, participate in consensus, and finalize settlement of relays. Joining the validator set typically requires a competitive stake; the recommended entry is ≥150,000 POKT. For context, service nodes (suppliers) stake 60,000 POKT as a baseline.
Why it matters
Validators ensure liveness and finality of the network. By processing blocks and governance updates, they keep claims and proofs moving, stabilize tokenomics, and safeguard the reliability that applications and gateways depend on. Strong validator participation makes Pocket’s usage-based settlement credible and trustworthy.
Incentives
Validators earn block rewards and transaction fees in POKT. Rewards scale with uptime, participation in consensus, and remaining inside the active set, ensuring that validators are incentivized to maintain performance and reliability.
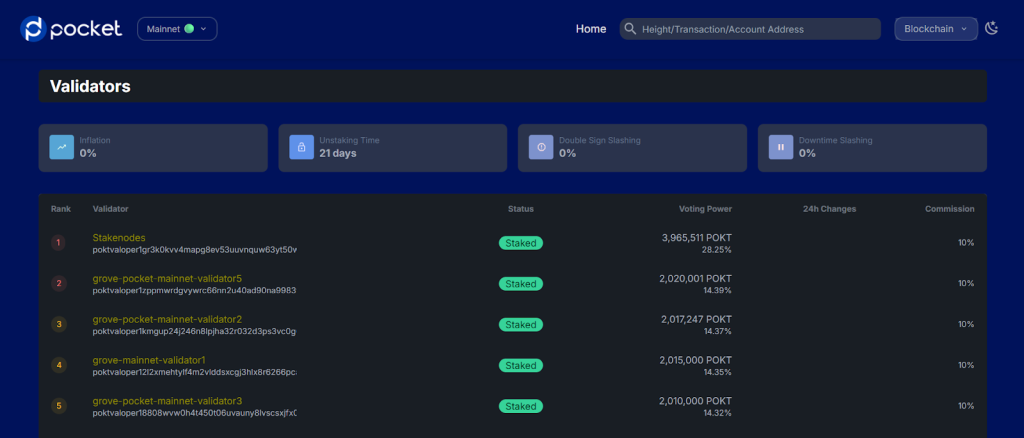
Validators on Pocket Network. Source: Pocket Explorer
Tools and Guides
- Validator Cheat Sheet (~15 min) — Quick setup from keys to staking.
- Validator Walkthrough (advanced) — Detailed step-by-step guide.
- Full Node Script (~10 min) — Build a baseline node to support validation.
- Hardware & Ops Requirements — Production considerations and FAQs.
- Blog post — Setting Up a Pocket Node on Shannon
Incentives at a Glance
In Shannon, every relay starts with Applications burning POKT and ends with rewards distributed across Gateways, RelayMiners, Validators, and the DAO. Each actor has a distinct role in the cycle, and together they close the loop that keeps requests moving and the network accountable. The table below gives a high-level view of how those roles connect.
| Role | How rewards/costs flow | Notes |
| Application | Burns POKT to pay for usage (in compute units). | Predictable costs; indirect upside if paired with your own Gateway (rebates). |
| Gateway | Qualifies for volume rebates (10–40% of daily CU spend, pro-rata, capped by DAO budget). | Rebates scale with daily throughput; settled quarterly. |
| RelayMiner | No direct rewards; earns indirectly by enabling settlement. | Valid proofs unlock Supplier payments; missed/invalid proofs mean forfeiture. |
| Supplier | Earns usage-linked rewards per valid relay served. | More reliable uptime/latency = more traffic = more rewards. |
| Service | Rewards flow via Supplier track; every request converts to CUs and is settled on-chain. | Can expose RPC, APIs, or AI inference endpoints; QoS filters invalid responses. |
| Validator | Earns block rewards + fees for consensus participation. | Must stay inside active set with competitive stake and uptime. |
What you can actually build in a weekend (project ideas)
If you’re pointing this post at hackathon participants, these are the “shippable by Sunday” ideas that map cleanly to the roles above:
1) Roll-your-own “RPC as a product.”
Gateway + RelayMiner + 2–3 Suppliers for chains your users care about. Add API keys, a lightweight billing page, and a status dashboard. Use the Gateway & Application cheat sheet to stake the app/gateway and wire a test relay; use the Supplier & RelayMiner cheat sheet to stand up the supply side. Bonus: demonstrate how QoS drops misbehaving endpoints
2) An AI agent with verifiable chain reads.
Publish a Service for an open-weight model, expose an OpenAI-compatible interface behind PATH, then prove your agent refuses non-quorum archival results. Start with the Service Creation Cheat Sheet, configure PATH QoS for archival checks (QoS overview), and show a mismatched node being filtered.
3) Indexer → Public Service.
Wrap your indexer (or subgraph) as a Service behind PATH. Provide two tiny client examples (one web, one server) to show how others can consume it with your Gateway URL + key. Use the Service Creation Cheat Sheet plus the QoS guides to decide what, if any, checks make sense for your data.
4) Param-aware ops bot (validators).
Run a Validator and publish a simple bot that watches tokenomics/params and announces changes (e.g., relay mining difficulty or CUTTM multipliers) to a channel used by app and gateway operators. Use the Validator Cheat Sheet to get online, and the Protocol Economics Parameters page as your canonical reference.
Closing Thoughts
Shannon turns Pocket into more than infrastructure—it’s a builder’s playground where every role, from gateways to validators, adds up to a stronger network. Whether you’re here to experiment, launch a product, or secure the protocol, the tools are in your hands and the incentives align with real usage. Start small, ship fast, and remember: every relay you run pushes open access to data a little further.
👉 Explore the tools and guides shared in this post, and if you need help along the way, reach out on Discord—our team is always on standby to assist.