Scaling decentralized networks can be challenging due to performance limits like low transaction speeds and high fees. Popular blockchain networks like Bitcoin and Ethereum process far fewer transactions per second (around 7 and 15-20 TPS, respectively) than native systems like Visa (65,000 TPS), opening the door to network competition on throughput and cost.
As decentralized networks grow, they must balance scalability, performance and security – as well as decentralization – while avoiding bottlenecks and inefficiencies. Without the right strategies, issues like latency, high operational costs, and uneven resource distribution can hinder adoption.
Much like increasing inference time or quality of training data improves the success of AI agents, Web3 networks also benefit from a few proven strategies for scaling. In this blog, we detail 8 proven case studies:
- Choose the Right Consensus Mechanism
- Scale Network Nodes
- Implement Layer-2 Solutions
- Monitor Network Health
- Build Modular Systems
- Apply Zero-Trust Security
- Speed Up Data Transfer
- Add Privacy Features
Summary Analysis: Comparing Key Web3 Network Scaling Techniques
Decentralized networks use various scaling techniques to solve the scalability trilemma. Each method addresses specific challenges, from increasing transaction throughput to improving network privacy. Below is a comparison of key techniques, their benefits, and examples of networks implementing them:
| Technique | Key Benefit | Example Network |
| Proof-of-Stake | Higher TPS, lower energy use | Ethereum 2.0 |
| Sharding | Parallel transaction processing | Zilliqa, Ethereum 2.0 |
| ZK-Rollups | Privacy, high security | Polygon Zero |
| Monitoring Tools | Prevent outages, optimize nodes | Chainlink, Cosmos |
| Modular Design | Simplified scaling | Polkadot, Celestia |
These strategies help decentralized networks scale efficiently while maintaining security and decentralization. Start by analyzing your network’s bottlenecks and implementing the most impactful solutions.
Scaling Strategies: How Layer-2 Solutions and Other Techniques Optimize Decentralized Networks
Decentralized networks leverage various off-chain and on-chain scaling strategies to achieve scalability without compromising security and decentralization. Layer-2 solutions, modular architectures, and optimized network designs enhance performance and efficiency. Below, we explore eight key strategies that help decentralized networks scale effectively while maintaining reliability and resilience.
1. Select the Right Consensus Method
Due to its limitations, Bitcoin’s Proof-of-Work (PoW) is not ideal for most modern applications.
Types of Consensus Methods
Over time, consensus mechanisms have expanded, offering various scaling capabilities. Here’s a quick comparison:
| Mechanism | Performance | Energy Use | Security Level | Example Network |
| Proof of Work | 7 TPS | Very High | Highest | Bitcoin |
| Proof of Stake | Up to 100,000 TPS | Low | High | Ethereum 2.0 |
| Delegated PoS | 4,000 TPS | Low | Medium | EOS |
| BFT Variants | 1,000 TPS | Low | High | Algorand |
For example, Ethereum’s shift to Proof-of-Stake (PoS) in 2022 cut energy use by an incredible 99.95% while significantly increasing transaction capacity, though arguably at a small cost to network security. Similarly, ThunderCore’s FastLane hybrid BFT consensus achieves over 4,000 transactions per second.
But improving throughput isn’t just about consensus mechanisms. Structural upgrades like sharding also play a key role.
Sharding for Better Performance
Consensus mechanisms set the baseline, but sharding can dramatically boost capacity by processing transactions in parallel across multiple chain segments. Zilliqa achieved 2,828 transactions per second using just six shards. Ethereum 2.0 aims even higher, planning 64 shards to reach its throughput targets.
However, sharding comes with its hurdles:
- Cross-shard communication: Secure and efficient communication between shards requires advanced solutions like crosslinks and data availability proofs.
- Security risks: Fewer validators per shard can make them more vulnerable to attacks. Ethereum 2.0 addresses this by randomly assigning validators.
Algorand’s pure proof-of-stake combined with BFT is another example of efficiency. It offers transaction finality in just 4.5 seconds.
For projects aiming to scale, the key is to find the right balance: boosting performance while managing the added complexity and security demands of advanced consensus models.
2. Scale Network Nodes
Expanding on consensus mechanisms and sharding, Network Nodes are key to boosting system capacity while improving decentralization. These processes include:
Set Up Node Auto-Scaling
Auto-scaling helps networks handle fluctuating workloads by tracking metrics like transaction queue lengths and processing times. Smart contracts, combined with oracles, can automatically trigger scaling events. To fine-tune this process, set clear thresholds, cool-down periods, and maximum node limits, and ensure rapid synchronization.
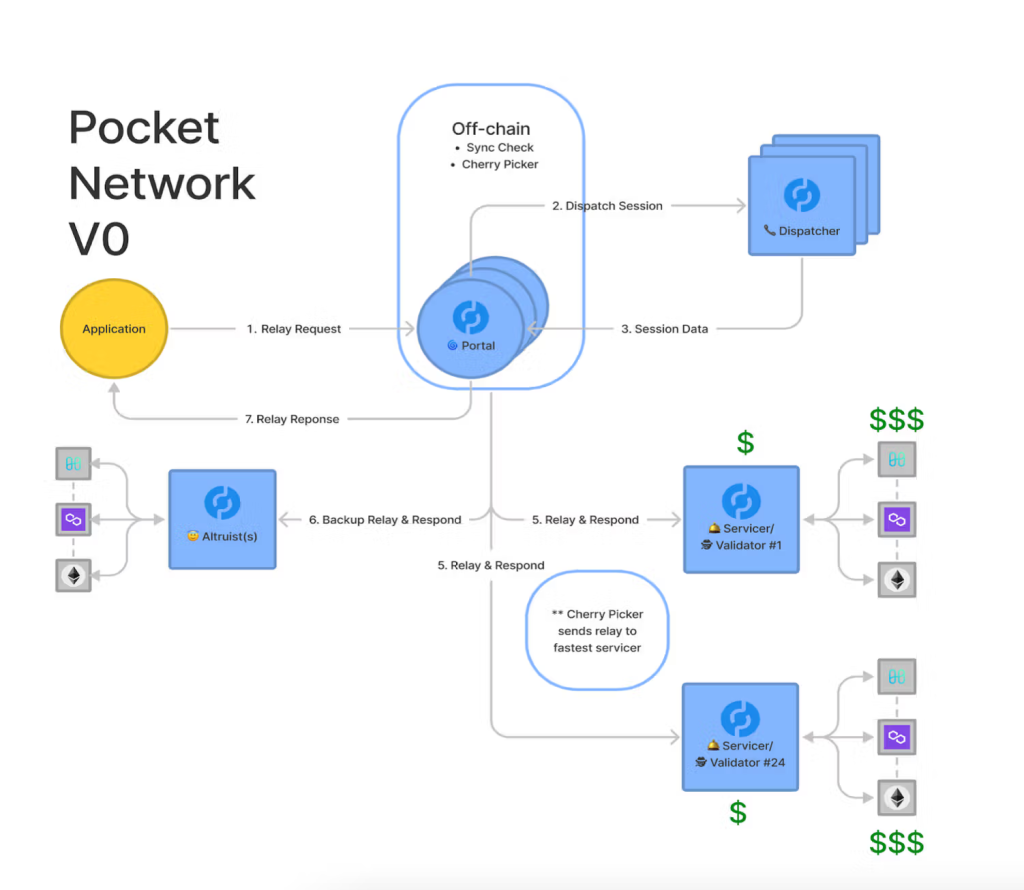
Pocket Network has demonstrated the power of dynamic scaling through its decentralized RPC infrastructure, efficiently distributing requests across thousands of independent nodes. This ensures that demand spikes are handled seamlessly while maintaining high availability and low latency.
Another great example is Algorand, which uses its pure proof-of-stake protocol to assign node committees for each block dynamically. By implementing dynamic scaling, workloads can be evenly distributed across nodes, maintaining efficiency and preventing congestion.
Balance Network Load
Efficient load balancing ensures decentralized networks handle high traffic without bottlenecks. Techniques like consistent hashing, gossip protocols, and sharding distribute workloads effectively. Zilliqa, for example, uses sharding to process transactions in parallel, achieving over 2,800 TPS.
Similarly, Pocket Network optimizes load distribution through its Shannon protocol, dynamically routing RPC requests based on real-time performance metrics. This prevents congestion, reduces latency, and ensures efficient node utilization. Additionally, permissionless gateways enable decentralized applications to access multiple RPC providers, further enhancing scalability and resilience.
Set Node Rewards
Incentivizing node operators ensures active participation and maintains a high-performance network. Performance-based rewards encourage high uptime, fast transaction processing, and reliable responses. Cosmos Network, for example, rewards validators based on stake size, uptime, and governance participation.
Conversely, Pocket Network has built a robust incentive model through its relay mining system. Node operators earn rewards proportionate to the number of serviced relays. This system ensures that nodes remain engaged while maintaining a decentralized and censorship-resistant RPC infrastructure.
3. Use Layer-2 Solutions
After scaling nodes, Layer-2 solutions offer another way to reduce congestion on the main blockchain without compromising decentralization. These “side-chains” handle transactions off the main network blockchain, increasing efficiency and lowering costs while keeping the security of the base layer intact.
Comparing Layer-2 Options
Layer-2 solutions come in different forms, each designed for specific use cases. For example, State Channels are perfect for gaming and micropayments, where frequent transactions occur between the same participants. Optimistic rollups, such as Arbitrum, can lower transaction fees by up to 100x compared to the base layer. Arbitrum itself processes more than 275,000 transactions daily.
For maximum throughput, ZK-rollups are a standout option. Take ZK-Sync as an example – it can handle up to 20,000 transactions per second and offers instant transaction finality. This capability makes it ideal for applications like decentralized exchanges or high-frequency trading.
| Layer-2 Type | Best For | Key Advantage | Trade-off |
| State Channels | Micropayments | Low latency | Limited participants |
| Optimistic Rollups | General dApps | Easy integration | Withdrawal delays |
| ZK-Rollups | Privacy-focused apps | High security | Complex implementation |
A great example of Layer-2 in action is Uniswap’s deployment on Arbitrum and Optimism. Within three months of launching in May 2023, these L2 dApps handled over 60% of Uniswap’s total trading volume. This reduced fees by 10–100x and increased daily active users by 150%.
When choosing a Layer-2 solution, consider these factors:
- Transaction volume: How many transactions do you expect to handle?
- Security needs: Do you require immediate confirmation, or can you tolerate dispute periods?
- Development complexity: Does your team have the technical expertise for implementation?
- User experience: How will it affect transaction speed and costs for your users?
The total value locked (TVL) in Layer-2 solutions reached approximately $51.5 billion in November 2024.
4. Monitor Network Health
Keeping a close eye on network health is crucial for scaling decentralized networks effectively and securely. Modern monitoring tools can pinpoint bottlenecks, prevent outages, and maintain reliable service across all nodes. The following are ways to optimize a decentralized network for scaling:
Track Network Metrics
Once transaction layers are optimized, continuous monitoring ensures consistent performance. Focus on critical metrics to maintain efficiency. For instance, Ethereum 2.0 aims for 100,000 transactions per second with 12-second block finality times. Key metrics to monitor include:
- Performance: Transaction throughput, Block time
- Reliability: Node uptime, Consensus participation
- Resources: CPU, Memory, Bandwidth usage
- Security: Fork rate, Chain reorganizations
For example, in June 2023, Chainlink overhauled its monitoring system. By integrating Prometheus and Grafana, they cut incident response time from 45 minutes to just 12, improving network stability by 73% in only three months.
In 2024, Tenderly significantly enhanced its blockchain monitoring capabilities by integrating over 25 rollup networks, providing full-stack infrastructure support for both Layer 1 and Layer 2 solutions.
5. Build Modular Systems
Modular systems enhance network efficiency by separating core functions—execution, consensus, and data availability—into specialized components. This system improves performance by reducing bottlenecks, simplifies maintenance by allowing independent upgrades, and streamlines scaling by enabling networks to adjust resources dynamically. These steps include:
Split Core Functions
Decentralized networks can perform better when their core functions are separated. Ethereum 2.0 is a good example, dividing its architecture into distinct consensus and execution layers. This separation allows each part to be fine-tuned independently. Similarly, Polygon’s modular approach reduced gas fees by 90% and increased transaction throughput by 1000x.
Here’s a breakdown of key network layers:
| Layer | Primary Function | Example Implementation |
| Consensus | Network agreement | Proof of Stake mechanisms |
| Data Availability | Information storage | Celestia’s data sampling |
| Execution | Transaction processing | Layer-2 rollups |
| Settlement | Final validation | Base chain verification |
Celestia’s testnet highlights the benefits of this design. It achieved 10x higher throughput by allowing light clients to verify blocks without downloading all the data.
Once the core functions have been streamlined, the next step is ensuring smooth communication between these modules.
Connect Network Parts
Separating functions is only half the job—ensuring these modules communicate effectively is just as important. Poor connectivity can compromise network performance. The Cosmos Network addresses this challenge with its Inter-Blockchain Communication (IBC) protocol, enabling smooth interaction between blockchains.
Here are some techniques to improve module connectivity:
- Use distributed message queues like Apache Kafka for asynchronous communication.
- Deploy API gateways to enhance cross-module security.
- Implement service discovery tools to support dynamic interactions between modules.
Polkadot offers another example of this approach. Its relay chain manages consensus and security, while parachains handle specific applications. This setup allows for tailored optimizations while keeping the overall network secure.
6. Implement Zero-Trust Security
Zero-trust security ensures every user, device, and system undergoes continuous verification, eliminating inherent trust–a crucial element for secure, modular network design.
Verify User Identity
Decentralized networks rely on layered verification to balance security and scalability. Sovrin uses decentralized identifiers (DIDs) and zero-knowledge proofs to authenticate users while preserving privacy. The Internet Computer employs chain key cryptography for scalable identity verification.
Here’s a breakdown of key verification layers:
| Verification Layer | Function | Example |
| Authentication | Confirm user credentials | Multi-factor authentication |
| Device Trust | Verify connecting devices | Hardware attestation |
| Network Access | Control connection points | Micro-segmentation |
| Transaction Validation | Ensure operation legitimacy | Cryptographic proofs |
To further strengthen access control, you can employ:
- Time-Based Permissions: Grant temporary access based on conditions, reducing exposure.
- Automated Security Policies: Platforms like Tezos optimize security through automation.
- Multi-Party Validation: Cosmos’s Tendermint consensus ensures high-risk actions require multiple validators, eliminating single points of failure.
Pocket Network employs a decentralized user verification and security approach, primarily utilizing Application Authentication Tokens (AATs). These tokens authorize applications to access the network without exposing private keys, ensuring secure interactions between applications and nodes.
7. Speed Up Data Transfer
Once you’ve optimized consensus and node performance, the next step in scaling decentralized networks is improving data transfer. Faster data transfer means quicker transactions and a smoother user experience.
Data latency plays a critical role in the performance and reliability of Pocket Network’s decentralized infrastructure. Key aspects include:
- User Experience: Ensures fast responses for applications, improving interactivity.
- Network Efficiency: Reduces node wait times, enhancing throughput.
- Reliability: Maintains stable and consistent service performance.
- Scalability: Supports growing application demand without performance loss.
Reducing latency through proximity-based node selection and efficient message-sharing protocols enhances data retrieval and transaction speeds in decentralized networks.
Choose Nearby Nodes
Selecting nodes based on proximity can significantly reduce latency. For instance, IPFS leverages libp2p’s proximity-aware peer selection for its nodes services, slashing retrieval times by up to 60%. Similarly, Filecoin‘s Lotus client has shown a 35% improvement in content retrieval, cutting the average file retrieval time from 3.2 seconds to 2.1 seconds across more than 3,500 storage providers. Alongside node proximity, refining message protocols is another way to boost transfer speeds.
Improve Message Sharing
Fine-tuning message-sharing protocols is another essential step to reduce latency further. Efficient propagation protocols help data move faster across the network. For example, the Hashgraph consensus algorithm uses a gossip protocol to deliver better throughput.
Some key techniques include:
- Bloom Filters: These compress transaction data, reducing the amount of data that needs to be shared during block propagation
- Erasure Coding: This method enhances reliability while cutting down on redundancy.
- Advanced Pub/Sub Systems: Tools like Filecoin’s libp2p pubsub enable updates to spread almost instantly.
Additionally, UDP-based protocols such as QUIC can reduce connection times. When paired with smart node placement, these methods have been shown to cut message propagation times from 2.5 seconds to just 0.8 seconds in a 1,000-node network.
8. Add Privacy Features
Privacy becomes a critical concern when scaling decentralized networks due to the increased risk of data leaks. Implementing strong privacy measures involves careful decisions about how and where data is processed.
Pocket Network enhances privacy through decentralized infrastructure, eliminating single points of failure and reducing data exposure. It follows a data minimization approach, ensuring no user information is stored and mitigating the risk of leaks. Additionally, partnerships with privacy-focused projects like Automata Network introduce encrypted data transfers and private transactions, strengthening security as the network scales.
Other key strategies for achieving and optimizing privacy in decentralized networks include:
Choose Processing Location
Deciding between on-chain and off-chain processing impacts both privacy and network performance. Here’s how they differ:
- On-chain processing ensures transparency and auditability but can expose more data and increase network congestion. It’s ideal for public transactions.
- Off-chain processing provides better privacy and reduces network load, though it may sacrifice some transparency. This is better suited for handling sensitive computations.
For example, the Oasis Network employs off-chain processing in its “Confidential ParaTimes” system, using Intel SGX secure enclaves to execute smart contracts while keeping the network efficient privately.
These processing strategies pave the way for integrating encryption methods that protect data without compromising performance.
Use Advanced Encryption
Encryption technologies play a key role in maintaining privacy while ensuring functionality. Two standout approaches are:
- Zero-Knowledge Proofs (zk-SNARKs): Polygon’s Polygon Zero project showcases how zk-SNARKs can enhance privacy. Their system cut transaction verification times from 5 minutes to just 10 seconds, significantly lowering gas fees by 98% compared to Layer 1.
- Homomorphic Encryption: This method allows encrypted data to be processed without decryption, offering robust security. Ocean Protocol uses this approach for compute-to-data access, protecting sensitive information. However, it is computationally demanding and may be slower than plaintext operations.
Performance trade-offs to keep in mind:
- zk-SNARKs may increase processing times by 10–100× but offer rapid verification.
- Homomorphic encryption operations can be 1000–1,000,000× slower than plaintext operations.
To strike a balance, apply these encryption techniques selectively to critical operations. This approach ensures data privacy while maintaining scalability and network efficiency.
Conclusion: Next Steps for Network Scaling
As decentralized networks grow, scaling requires a step-by-step approach. With the blockchain market projected to reach $988.83 billion by 2032, organizations must choose scaling strategies that align with their specific needs.
Start by analyzing your network’s performance. Identify bottlenecks and focus on solutions that provide the most significant immediate improvements. For instance, layer-2 solutions can significantly boost throughput, while sharding increases processing power. This initial evaluation lays the groundwork for a structured scaling plan.
Here’s a suggested roadmap for scaling:
| Phase | Focus Area | Key Actions | Expected Outcome |
| Initial | Performance Analysis | Monitor metrics, pinpoint bottlenecks | Clear priorities for scaling |
| Foundation | Core Infrastructure | Upgrade consensus methods, scale nodes | Greater network stability |
| Optimization | Advanced Features | Introduce layer-2 solutions, add privacy tools | Better user experience |
| Maintenance | Long-term Growth | Set governance, refine update processes | Consistent network progress |
These steps build on earlier strategies like consensus upgrades, node scaling, and security enhancements.
Robust monitoring systems are essential to adapt to evolving network demands throughout scaling. Recent advancements, such as Ethereum’s Dencun upgrade and the proliferation of Layer 2 solutions, have significantly reduced transaction costs and improved scalability.
Integrating emerging technologies like zero-knowledge rollups and AI-driven optimizations can further enhance performance. Implementing a treasury system funded by network fees ensures sustainable development. By embracing these innovations, networks can maintain efficiency, security, and resilience in a rapidly evolving landscape.

